Analyse Kubernetes Security Findings with New Relic Vulnerability Management
At Bion Consulting, we care about security and always build using best security practices. I give my complete attention to someone who says something about “Security” because security is a never-ending journey. So when New Relic published its Vulnerability Management feature, I did the same.
In the modern IT world, security is an essential element. Security must be considered a crucial requirement to build high-quality, seamless, reliable services. But it is challenging in today's fast-paced technological environment, complex systems with hundreds of APIs, 3rd party and open-source tools. Integrating new software composition analysis (SCA) tools like kube-bench into our system is an option to provide security. However, if a team is not currently using any security tool, integrating a new tool will cause extra workload to teams and laborious tasks to complete. To optimize security operations with a great return on investment metrics, the new feature of New Relic comes into play: Vulnerability Management. New Relic is not adding a new tool to your ecosystem and not creating additional noise with Vulnerability Management. With Vulnerability Management, either you can integrate any 3rd party security tool to your New Relic account, or via New Relic APM agent, you can directly start using the Vulnerability Management feature. The solution is collecting vulnerabilities and serving all information in one place for detailed consideration and efficient management of full-stack security operations, as security must be reviewed as a complete picture. Vulnerability Management provides in-depth analytics solutions for application vulnerabilities and guidelines for remediation based on known issues.
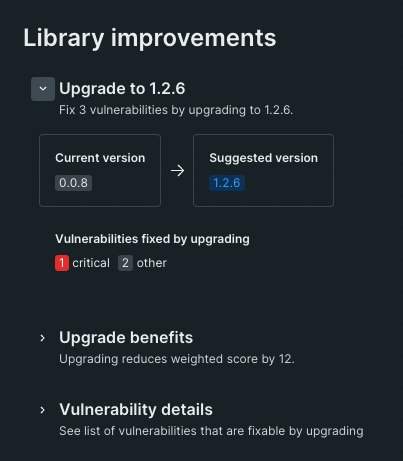
Vulnerability Management provides analysis capabilities for application and infrastructure vulnerabilities and guidelines for remediation based on known issues. Additionally, you can integrate external security tools to import data from different sources. You can centralize your security management to view, assign to devs and fix vulnerabilities. Currently, it’s generally available now, free of charge for data plus plans and free account users, so give it a chance if you’re looking for this kind of security tool.
Once you integrate the Vulnerability Management solution into your security operations, you will obtain the utmost value in the following aspects of your security operations:
- Vulnerabilities will be prioritised and fixed by the tech teams conveniently, as the tool can show each security subject in one place in the order of importance of the vulnerabilities.
- Actionable insights will be shared to create a deeper understanding of security operations and illuminate the teams about these operations.
- The best practices will be driven for risk remediation and accountability, and integrated security workflow will be created across the entire software lifecycle.
Prerequisites to use Vulnerability Management
- Available for full platform users
- Vulnerability Management isn't available to HIPAA-enabled accounts, or FedRamp-enabled accounts. But this will change over time, and more capabilities will be added to this feature.
Vulnerability Data Integration Methods
- APM Agent Integration: New Relic APM agent automatically detects CVEs in the libraries used by your service. With the help of this way of integration, you will eliminate the laborious tasks for data export and optimize it in an automated way.
- Third-Party Integration: Using 3rd party integration, you can get CVEs detected by third-party integrations such as AWS Security Hub, Dependabot, Snyk, or Trivy.
- Security Data API: This method enables integration of unsupported third-party tools. It allows users to choose their 3rd party security tools.
Prerequisites
- Kubernetes Cluster or Minikube, Version >= 1.23
- New Relic account in the US (Vulnerability Management is not available in the EU)
- kubectl
Kube-Bench Tool Overview
Kube-Bench is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark. I’ll use it to generate a vulnerability report. This report will be the source for a custom python script that forwards vulnerabilities to the New Relic Vulnerability Management Security Data API. Check the following example test generated by kube-bench tool.
|
{ |
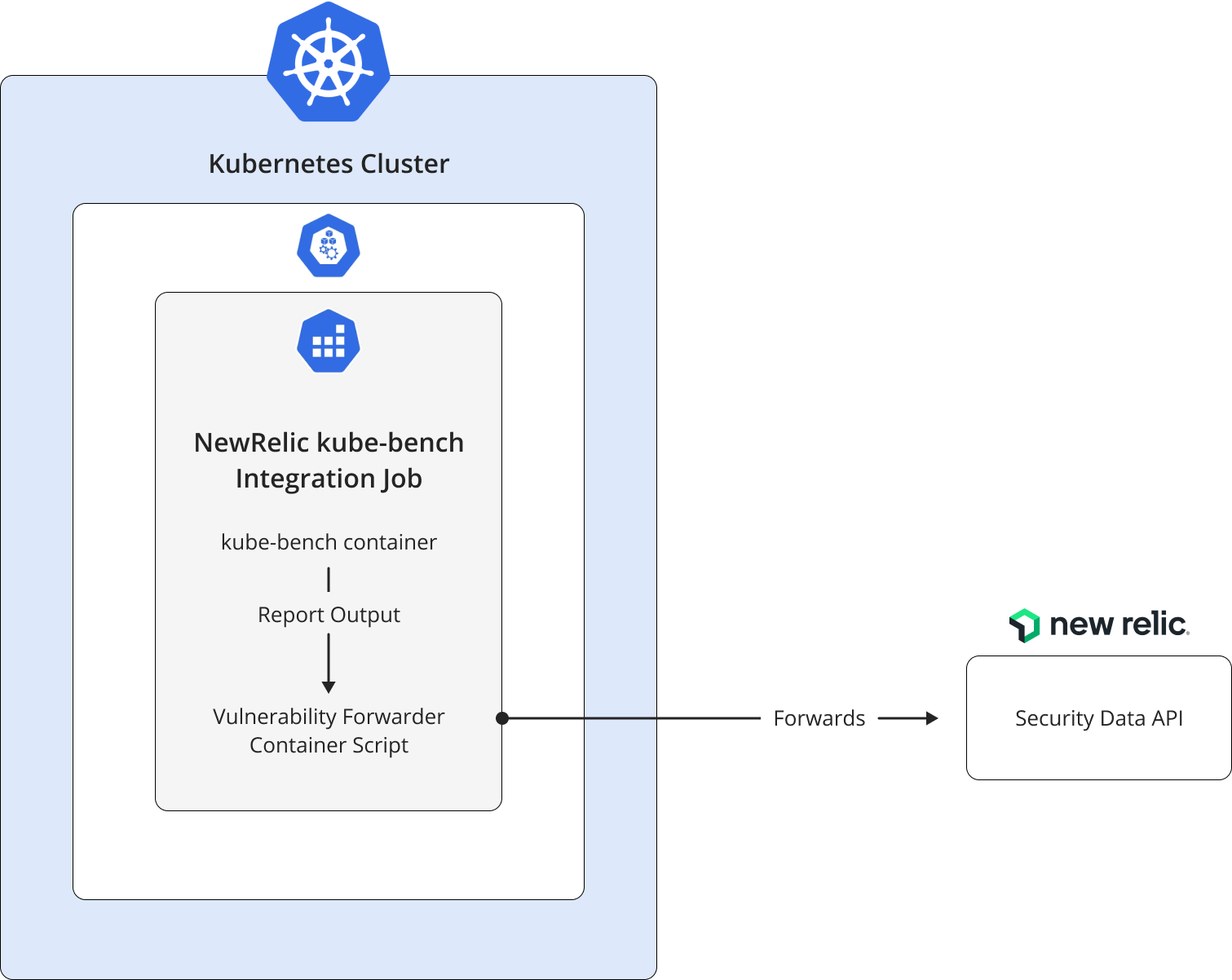
Architectural Diagram
We have two main tasks in total. The first one is running kube-bench to generate vulnerability reports, and the second is running a custom python script to send these findings to the New Relic Security Data API. We decided to run both of these tasks on Kubernetes to simplify the user process.
Setup Steps
- As a starter, let's install Minikube for the local Kubernetes cluster. From a terminal with administrator access, run the following command:
|
# minikube start --cpus 2 --memory 2g --kubernetes-version=v1.23.0 |
- To start using kube-bench for generating a vulnerability report and sending data via the New Relic security API, first clone the repository, then edit Kubernetes secret YAML in the “job.yaml” file using your New Relic API key. Build dockerfile and push it to your repository. Change the image name in “job.yaml” file. To create and manage your New Relic API keys use the API keys UI page. Lastly, in the job.yaml file, edit the CLUSTER_NAME environment variable with your current cluster name.
- After completing the above steps, we will deploy a Kubernetes job object to set up kube-bench and 3rd party data integration in one step. The Kubernetes job object first runs kube-bench as an init-container and completes the Kubernetes security scan. After the scan is completed, it will write the output to a file. Lastly, a python script will parse the JSON output and send it to the New Relic Vulnerability Management dashboard via security API.
|
# kubectl create -f job.yaml |
- You can find all the code provided in this article inside of this GitHub repository: https://github.com/TeamBion/newrelic-kube-bench-integration
Dashboard and Alert Creation
Now, log in to New Relic to check 3rd party security data ingestion. To see the vulnerabilities found by kube-bench we need to check the vulnerabilities tab inside the Vulnerability Management feature.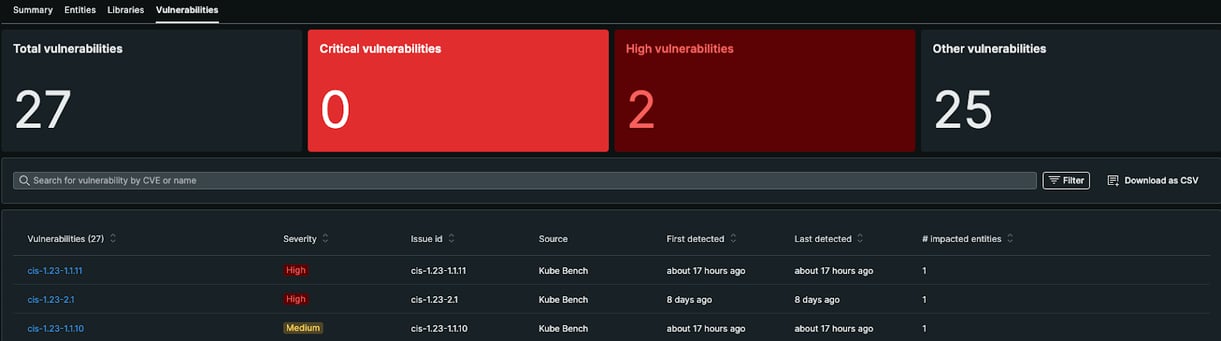
For a detailed overview, we can choose an individual vulnerability and see the details:
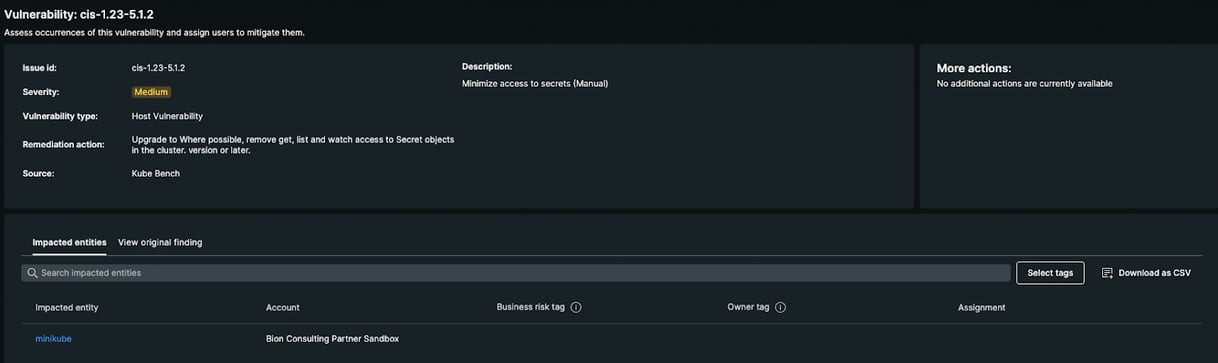
New Relic correlates vulnerabilities and entities present in our account. Under the “impacted entities” section, we can see the entities affected by this vulnerability:
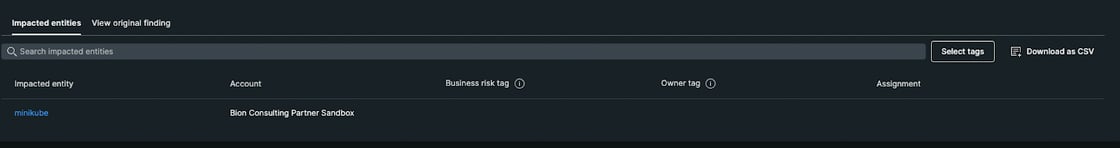
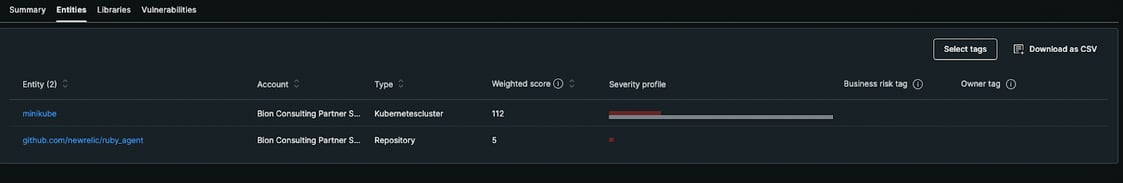
Lastly, the entities affected by the vulnerabilities can be seen individually by using this view. And the entities can be sorted in order of their weighted vulnerability scores. It gives the teams a chance to focus on the most vulnerable entity and decrease the attack surface.
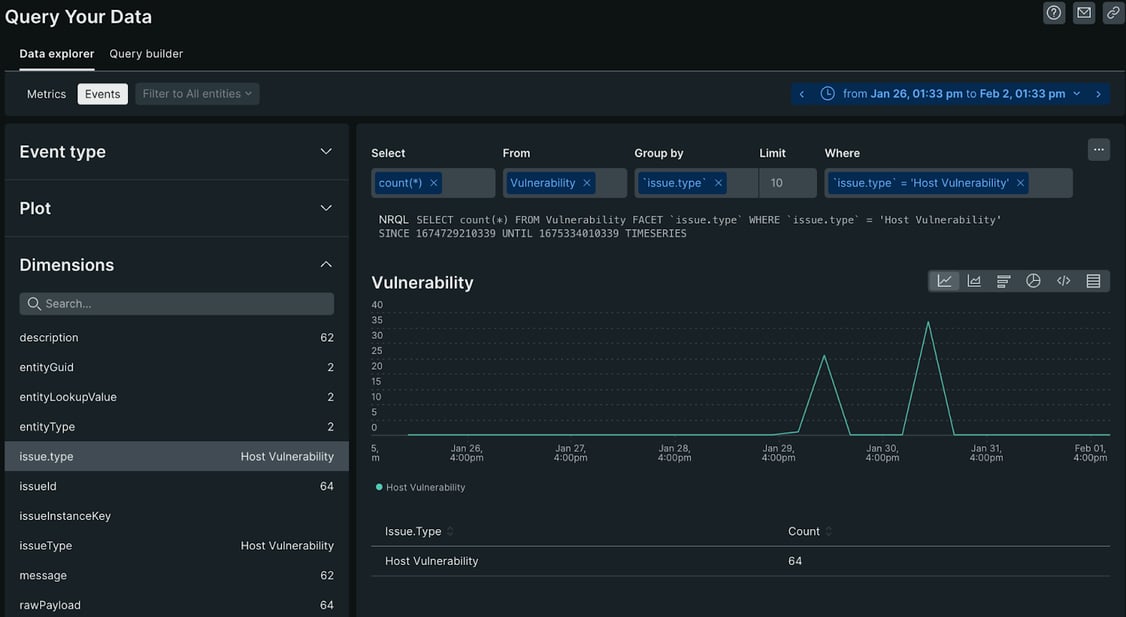
Another great capability of New Relic is creating queries over vulnerability data and creating dashboards with these queries. To perform this action, let’s click “Query Your Data” button under the left side menu, and start exploring your data.
Creating dashboards using these queries is also quite simple with New Relic. Click the three dots on the right side and click “add to dashboard” button.
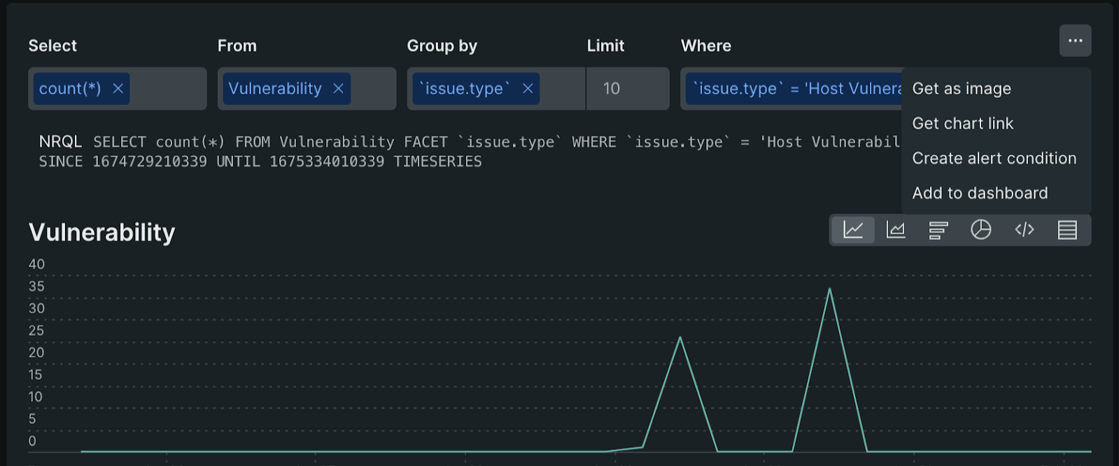
And under the “Dashboard” view on the left side, we can check the dashboard we created using queries. Finally, we can explore creating an alert using this dashboard data by clicking the three dots on the right side.
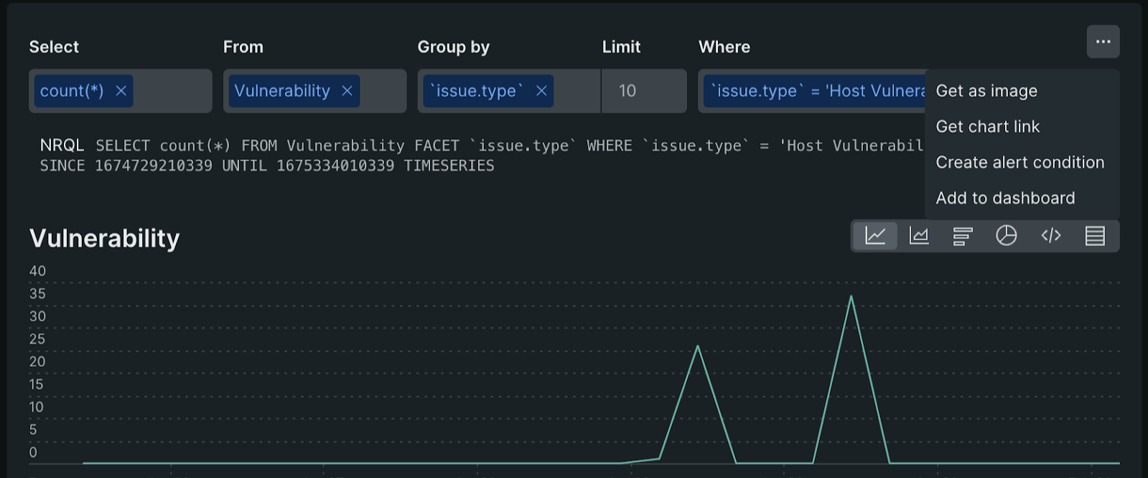
Finally, we can explore creating an alert using this dashboard data by clicking the three dots on the right side.
Benefits
Let's look at some statistics to understand the importance of integrating New Relic’s Vulnerability Management feature.
According to software security company Veracode found that on average, applications have about 15 vulnerabilities per application. Of these vulnerabilities, around 60% were considered to be of high or critical severity. The rate at which vulnerabilities are re-introduced into the codebase after they have been fixed can vary, but a study by Veracode showed that around 20% of vulnerabilities are re-introduced within a year of being fixed. Also, a study by NIST(National Institute of Standards and Technology) showed that the average time to remediate a vulnerability is around 45 days.
These statistics also show that regular scanning and prioritizing problems are vital for our applications in order to take quick action against security vulnerabilities. With the help of Vulnerability Management integration, we are able to scan our system constantly, prioritize security risk with entity correlation, take quick and safe actions via Vulnerability Management library update suggestions. We can create alerts to be notified if something unexpected comes up. In order to benefit from all these capabilities, it will be sufficient to integrate the New Relic APM agent into your system, or if there is a security tool you are already using, it will be enough to integrate it into your New Relic account.
Wrapping it up
This feature unifies insights and collaborates across our organization by importing data from security tools either using built-in quickstart integrations or using APIs to integrate data from any custom security source. It’s a tailor-made feature during the prioritisation of the vulnerabilities and assigning them to the team to resolve these issues. And in addition to all of these valuable capabilities, you don't have to deal with any complicated integration steps. You can simply use 3rd party security tools that you already use and benefit from and send data to New Relic dashboards via New Relic security API.
References:
https://youtu.be/0IDRwKUzadw
https://docs.newrelic.com/docs/vulnerability-management/integrations/intro/
https://docs.newrelic.com/docs/vulnerability-management/integrations/security-data-api/
