DevSecOps Consulting Services for Modern Cloud Platforms
Secure your software delivery pipelines with DevSecOps consulting focused on AWS, Kubernetes and CI/CD security. We help engineering teams reduce risk, protect software supply chains and implement compliance-ready security controls without slowing delivery.
.jpeg)
DevSecOps Consulting Services
We provide DevSecOps consulting services that help engineering teams secure modern software delivery pipelines without slowing development.
Our consultants work closely with developers, platform engineers, and security teams to integrate security across every stage of the SDLC — from secure architecture design and CI/CD security automation to cloud, Kubernetes, and software supply chain protection.
We focus on hands-on, automation-first DevSecOps, working directly in your environments to reduce security risk, enforce policy-as-code controls, and operate compliance-ready delivery pipelines in production.
What Our DevSecOps Consulting Covers
- CI/CD Security Consulting: Securing build and deployment pipelines with automated security controls, policy enforcement, secrets detection, and vulnerability scanning embedded directly into CI/CD workflows.
- AWS & Kubernetes Security: Hardening cloud infrastructure and Kubernetes platforms on AWS, including EKS cluster security, container image scanning, workload identity controls, and runtime protection.
- Software Supply Chain Security: Protecting applications from dependency and image risk through SBOM generation, open-source dependency analysis, image provenance controls, and policy-based enforcement.
- Infrastructure-as-Code & Cloud Security: Securing Terraform and Helm-based infrastructure with configuration scanning, drift detection, and compliance-as-code controls across cloud environments.
How Our DevSecOps Consulting Works
We take a hands-on, implementation-led approach to DevSecOps, working directly inside your environments to secure software delivery from code to production.
Our consulting model is designed to integrate seamlessly with existing teams, tooling, and workflows — focusing on measurable security improvements rather than theoretical frameworks.
1. Assess & Prioritise Risk
We start by reviewing your CI/CD pipelines, cloud infrastructure, Kubernetes environments, and software supply chain to identify the most critical security gaps and operational risks.
This allows us to prioritise controls that reduce risk without disrupting delivery velocity.
2. Implement Security Controls
We implement security directly into your delivery workflows, embedding controls where they provide the most value:
- CI/CD security gates and automated checks
- Policy-as-code enforcement
- Container and Kubernetes security controls
- Infrastructure-as-Code validation
All controls are implemented in a way that fits your existing engineering practices.
3. Enable Teams & Ownership
Rather than introducing security as a separate function, we work alongside developers, platform engineers, and security teams to establish clear ownership and shared responsibility.
This ensures DevSecOps practices are sustainable and adopted across teams.
4. Operate & Improve Continuously
Once controls are in place, we help teams operate secure, production-ready pipelines through continuous monitoring, feedback loops, and ongoing improvement.
Security becomes a continuous process — not a one-off project or audit exercise.
Outcomes of Our DevSecOps Consulting
Earlier Risk Reduction Across CI/CD and Production
By embedding security controls directly into CI/CD pipelines and production environments, we help teams identify and address risk early — before vulnerabilities reach customers or regulated systems.
Security Controls Without Slowing Delivery
Our hands-on DevSecOps consulting integrates automated security checks and policy-as-code enforcement into existing workflows, reducing rework and avoiding late-stage security bottlenecks.
Compliance-Ready and Operable Security
We help teams run secure, audit-ready delivery pipelines with clear ownership across engineering and security teams, supporting ongoing compliance and production stability.
Industries We Support with DevSecOps Consulting
Our DevSecOps consulting services are tailored to industries operating modern cloud platforms where security, compliance and delivery speed must work together.
Financial Services & Insurance: We help financial services and insurance organisations secure CI/CD pipelines and AWS environments with audit-ready workflows, policy-as-code enforcement and compliance-driven automation.
Our approach supports highly regulated, high-trust systems by embedding security controls directly into software delivery and infrastructure operations.
SaaS & ISV: We support SaaS and ISV teams running multi-environment CI/CD pipelines and containerised platforms by integrating DevSecOps controls that scale with rapid product growth.
Security is embedded into Kubernetes workloads, software supply chains and deployment workflows without slowing feature delivery.
Retail & E-commerce: For retail and e-commerce platforms, our DevSecOps consulting focuses on securing high-traffic, customer-facing systems while maintaining availability and deployment reliability.
We help teams protect cloud infrastructure, automate security checks and support zero-downtime release workflows during peak demand periods.
Travel & Hospitality: We work with travel and hospitality organisations operating distributed cloud environments and transaction-heavy systems.
Our DevSecOps consulting secures CI/CD pipelines, booking platforms and cloud infrastructure with automated controls designed for resilience, scalability and operational continuity.
Healthcare & Life Sciences: We help healthcare and life sciences organisations implement secure, compliant cloud platforms aligned with strict data protection and regulatory requirements.
DevSecOps controls are embedded into release workflows, infrastructure automation and platform operations to support controlled, auditable delivery processes.
Education & EdTech: For education and EdTech platforms, we provide DevSecOps consulting that supports scalable, multi-tenant architectures and secure release automation.
Our approach enables teams to deliver frequent updates while maintaining platform stability and protecting sensitive user data.
Startups: We work with startups and high-growth engineering teams to establish foundational DevSecOps practices early.
This includes secure CI/CD pipelines, cloud-native security controls and automation that supports rapid growth without introducing unnecessary operational overhead.
DevSecOps Tools & Practices Used
- Pre-Commit Hooks
- Static Application Security Testing (SAST)
- Software Composition Analysis (SCA)
- Artifact and Repository Scanning
- Infrastructure-as-Code Security
- Vulnerability Assessment
- Secrets Management & Credential Security
- IDE Security Plugins
- Dynamic Application Security Testing (DAST)
- Dockerfile Best Practices and Image Security
- Container and Kubernetes Configuration Security
- Compliance-as-Code
- Container Runtime Security
- Software Supply Chain Security
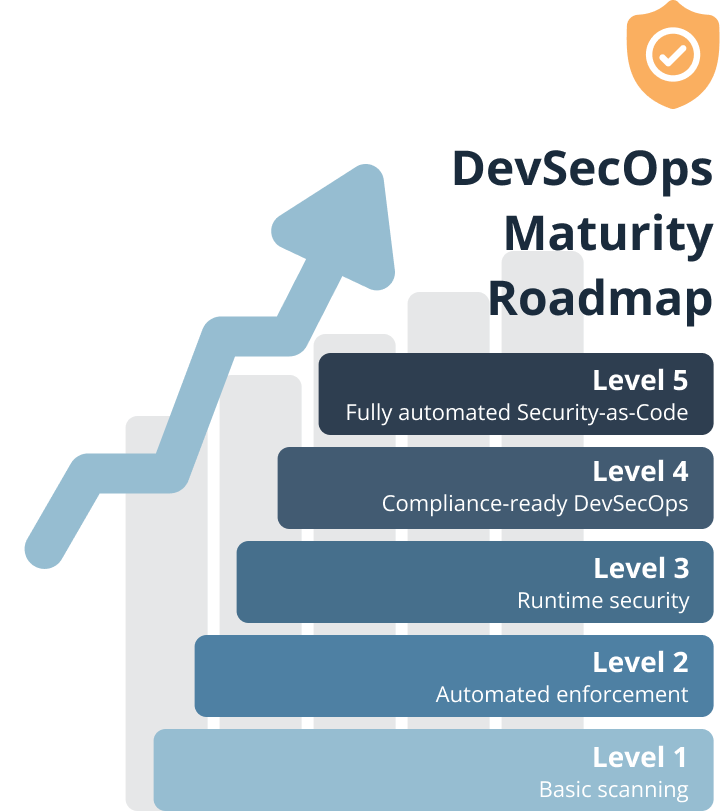
DevSecOps Maturity Roadmap
Security adoption is a journey. We help organisations mature from basic scanning to fully automated, policy-driven pipelines:
Level 1 — Basic scanning: SAST/SCA in CI
Level 2 — Automated enforcement: IaC + CI/CD security gates
Level 3 — Runtime security: monitoring, anomaly detection
Level 4 — Compliance-ready DevSecOps: audit trails, controls
Level 5 — Fully automated Security-as-Code
Your Trusted Partner in Secure Software Delivery
At Bion, we don’t just integrate security into DevOps pipelines — we partner with your teams to embed security into every stage of your software delivery lifecycle. Whether you're just starting with DevSecOps or refining a mature practice, our experts bring the guidance and tools to help you build with confidence.
Contact us today to review your CI/CD, AWS and Kubernetes security posture with our DevSecOps consultants and get clear, actionable next steps.


