Having More Secure AWS Environments with AWS Security Hub - Part 1
How secure do you think your cloud environment is? According to the 2021 Cloud Security Report by Aqua, there is a significant rise in the number of cloud misconfigurations.
Most of the misconfigurations in cloud environments are exposed buckets, misconfigured ACLs (Access Control Lists), permissive storage policies, unencrypted cloud storage, IAM (Identity and Access Management) misconfigurations, unencrypted data in traffic and open ports to the world.
In the research, they found that 82.4% of cloud environments had "open to the internet" issues. 92.1% of the users reported at least 1 issue with exposed buckets with approximately 70 days of remediation. Furthermore, 74.3% of the users had issues with unencrypted data in the cloud storage, and they implemented the changes on average every 3 months. Most importantly, more than half of the users had at least one case (e.g., Amazon EC2) with all ports open to all inbound traffic.
In this multi-part blog post, we are going to explain how you can improve the security of your AWS environment with AWS Security Hub and how to use it to set automated response and remediation. In the first part, we will cover the topics of How Security Hub works, Prerequisites, Setup, Cross-Region aggregation, Product integration and the second part will describe how you can set automated responses and remediations based on your findings.
AWS Security Hub!
Security Hub is an AWS service that shows you the security state of your environment based on industry standards and best practices by collecting data from across AWS accounts, services and supported third-party products. AWS Security Hub comes with four major benefits:
- Reduces the effort to collect and prioritize security findings
- Automatically runs continuous security checks based on AWS best practices and industry standards
- Provides a consolidated view of findings across accounts and provider products
- Has the ability to take automated actions on findings
How Security Hub Works
The AWS Security Hub can be enabled through the AWS Management Console, using the Security Hub API or AWS CLI. When you first start using Security Hub, AWS provides you with a 30-day free trial.
When you enable Security Hub, it immediately begins to consume, aggregate and prioritize findings from the AWS services and the integrations that you have enabled. However, it does not detect security findings that were generated before. Security Hub is a region-level service and so only receives findings from the region where you enabled it.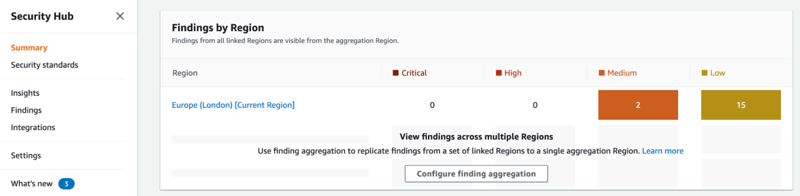
Predefined Security Standards
Security standards provide a set of related controls to determine compliance with regulatory frameworks, industry best practices, or company policies. Some security standards are available in the AWS Security Hub:
- Center for Internet Security (CIS) AWS Foundations Benchmark
- Payment Card Industry Data Security Standard (PCI DSS)
If you are using Security Hub with AWS Organizations integrated, the CIS and Foundational Security Best Practices standards are auto-enabled in new member accounts by default.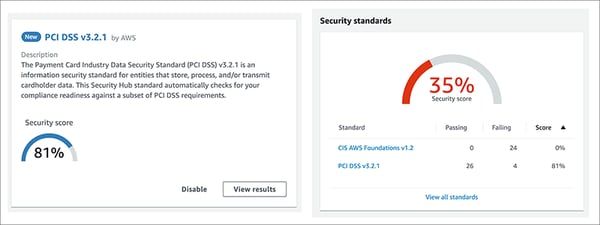
Prerequisites
Security Hub requires that AWS Config is enabled, and it uses AWS Config rules to complete security checks. Also, it strongly recommends that you enable AWS Organizations. When Organizations is enabled, Security Hub automatically detects new accounts as they are added to your organization.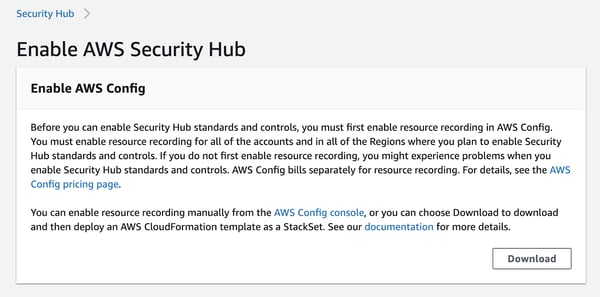
Setup
If you use integration with AWS Organizations, the organization management account designates a Security Hub administrator account and enables Security Hub automatically in that account. Then, the Security Hub administrator account enables organization accounts as member accounts and enables Security Hub automatically in those accounts also. If the Organization integration is not in place for managing the accounts, Security Hub must be enabled manually. You can then invite member accounts from the administrator account.
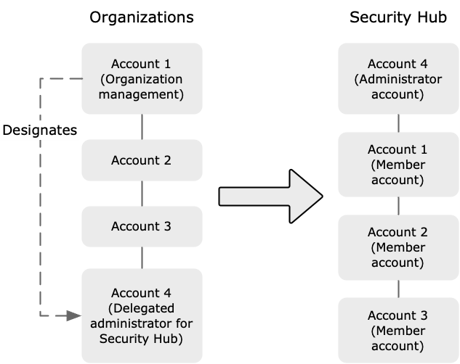
(Source: https://docs.aws.amazon.com/securityhub/latest/userguide/designate-orgs-admin-account.html)
Cross-Region Aggregation
Cross-Region aggregation allows you to manage all Security Hub data (findings, finding updates, compliance statuses, security scores) from multiple regions in a single aggregation region. To view cross-region security scores, your IAM user must have the following permissions:
- ListSecurityControlDefinitions
- BatchGetStandardsControlAssociations
- BatchUpdateStandardsControlAssociations
To enable cross-region aggregation, in the Security Hub navigation menu, go to Settings->Regions->Finding aggregation->Configure finding aggregation. AWS does not charge any additional cost for cross-region aggregation.
When cross-region aggregation is enabled, Security Hub also replicates updates to aggregated data between the linked regions and the aggregation region.
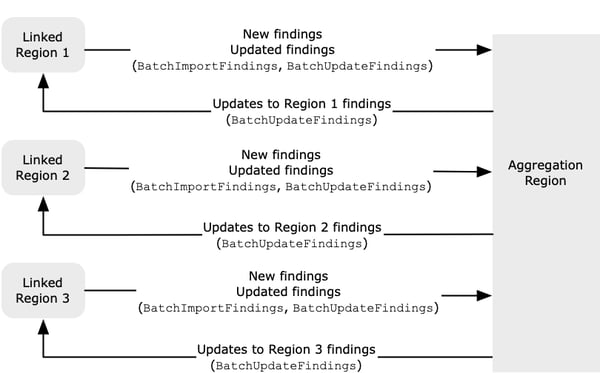
"If there are conflicting updates in the aggregation Region and the linked Region,
then the most recent update is used."
(Source: https://docs.aws.amazon.com/securityhub/latest/userguide/finding-aggregation-overview.html)
Product Integration
With Security Hub, you can aggregate security-finding data from AWS services and third-party products.
For AWS service integrations, the only step needed is to turn on the AWS service. The integration between Security Hub and the AWS service is automatically activated, and the service starts either sending findings to or receiving from Security Hub. You can check the link for the list of integrated AWS services.
Third-party product integrations can be activated under the Integrations page of the Security Hub console. They have an Amazon Resource Name (ARN) and send findings to Security Hub. Some of the third-party integrations are Aqua Security, Forcepoint, McAfee, Palo Alto Networks, Prowler, Sophos and Sysdig. You can find the full list here. Each partner has its own documentation explaining how to configure the product for AWS Security Hub.
In addition to AWS services and third-party products, Security Hub is also able to receive findings generated by other custom products. BatchImportFindings API operation allows you to send findings into the Security Hub. AWS provides a guideline and a checklist to set up a custom integration in Security Hub Partner Integration Guide.
Conclusion
In this part of the AWS Security Hub blog post series, we run through the key features of AWS Security Hub. It helps you gather security-finding data from across AWS accounts, services and supported third-party products into a single dashboard and view your AWS environment's security against industry standards and best practices.
In the next section, we are going to explain how you can set automated response and remediation based on the security findings to make your AWS environment more secure.
