The motivation of the Blog Post; In AWS, tagging is an essential part of cost visibility and security. Unfortunately, this can lead to a problem. Every single user on your AWS account can create resources with any keys/values. When you don’t control those tags keys/values, your cost visibility will decrease and eventually, it’ll create big problems. To solve this issue, we will create a control mechanism over our tagging strategy with the help of Tag Policies. If you would like to go beyond good intentions on tagging strategy, keep on reading!
Beyond Good Intentions
As Jeff Bezos often reminds us, “Good intentions don’t work, but mechanisms do.” Standardising on names, values, capitalisation, and punctuation is a great idea but challenging to put into practice. When tags are used to control access to resources or divvy up bills, small errors can create big problems!
Developers or other users may not comply with tagging strategies. How do you apply and enforce strict tag policies over your whole AWS Organisation?
Let’s find out!

What are AWS Organisations?
AWS Organisations help you centrally manage and govern your environment as you grow and scale your AWS resources. Using AWS Organisations, you can programmatically create new AWS accounts and allocate resources, group accounts to organise your workflows, apply policies to accounts or groups for governance, and simplify billing by using a single payment method for all of your accounts.
In addition, AWS Organisations is integrated with other AWS services so you can define central configurations, security mechanisms, audit requirements, and resource sharing across accounts in your organisation. AWS Organisations is available to all AWS customers at no additional charge.[1]
What are tag policies?
Tag policies are a type of policy that can help you standardise tags across resources in your organisation’s accounts. In a tag policy, you specify tagging rules applicable to resources when they are tagged.
For example, a tag policy can specify that when the CostCenter tag is attached to a resource, it must use the case treatment and tag values that the tag policy defines. A tag policy can also specify that noncompliant tagging operations on specified resource types are enforced. In other words, noncompliant tagging requests on specified resource types are prevented from completing. Untagged resources or tags that aren't defined in the tag policy aren't evaluated for compliance with the tag policy.[2]
Why “AWS Organisations Tag Policies” instead of “AWS Config”?
We could achieve remediation of uncompliant tags with AWS Config too. Both ways have advantages and disadvantages. AWS Config cannot instantly prevent the creation of uncompliant resources. When you define the AWS Config Rule, remediation action will work. Because of that, you will be billed partially. On the other hand, you could achieve more strict tag policies with AWS Organisations Tag Policy for free!

Example of the Tag Policy Scenario in Real-Life
Let’s assume that your organisation should follow a standardised tag key (costcenter) and tag value(bion-ec2-*) for EC2 service — services supporting tag policy enforcement at the time of writing this post[3].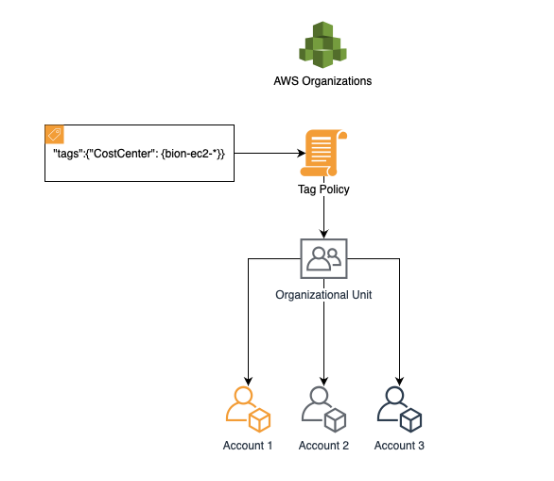
The requirements for the scenario are:
- Your organisation must have all features enabled.
- You must be signed in to your organisation’s management account.
- You need to enable the permissions that are listed in Permissions for managing tag policies.
Tag policy syntax and example tag policy
A tag policy is a plaintext file that is structured according to the rules of JSON. The syntax for tag policies follows the syntax for management policy types. For a complete discussion of that syntax, see Policy syntax and inheritance for management policy types. This topic focuses on applying the general syntax to the specific requirements of the tag policy type.
The following tag policy shows an example of tag policy syntax:
|
{ "ec2:elastic-ip", "ec2:fleet", "ec2:image", "ec2:instance" |
With this policy, we defined “costcenter” as a tag key and “bion-ec2-*” as a tag value. At the “enforced_for” section of the tag policy, we enforce the tag key and tag value within some of the ec2 resources. More policies could add up to the 10,000 character limit within one tag policy. Also, a crucial tip is that wildcards are only allowed in tag values. On the other hand, tag keys should not be longer than 128 characters and can only include the following characters.
“Tag keys must be between 1-128 characters in length. Valid characters are alphanumeric, separators, and these symbols _.:/=+-@.”
Tag Enforcement with Tag Policies in Action!
First things first, you should be part of an AWS Organisation. Let’s create our organisation in AWS Management Console.
Click on “Create an organisation.”
AWS Organisations home page
Great, now we are part of the organisation; the next step is to enable our organisation’s tag and service control policies.
To do that, select policies on the left-hand side. In the policies, click on service control policies and tag policies, then enable these policies.
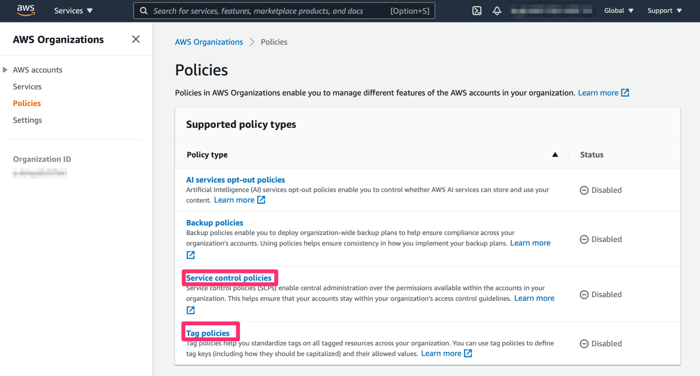
AWS Organisations Policies Section
After enabling service control and tag policies, you can see them as enabled in the policies section.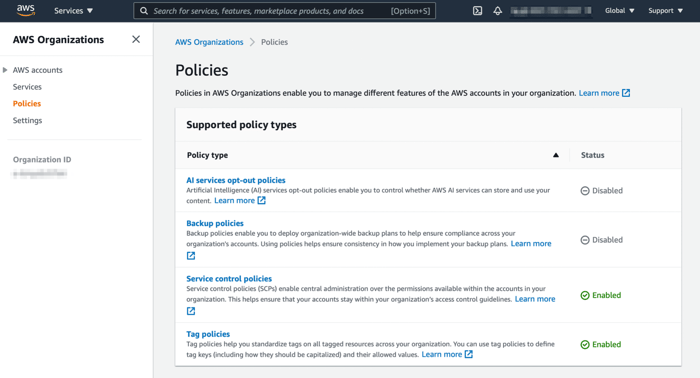
AWS Organisations Policies Section
Great! We are finished with prerequisites. As a next step, we will create our tag policy. After creating the tag policy, we need to attach it to the organisation unit or organisation root. If you attach the regarding policies to the organisation root, the policies will be applied for all OUs as shown below.
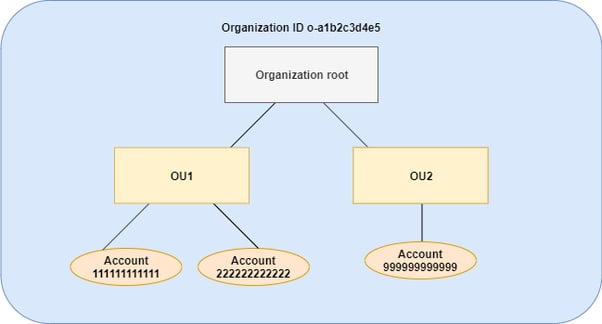
Example chart of the Organisation Hierarchy [4]
In this case, I’ll attach the tag policy to the organisation’s root.
Attaching Tag Policy to the regarding organisational unit.
Test Flight!
For testing of our tag enforcement, I’ll try to create an EC2 instance with a non-compliant tag. I used the costcenter tag key and non-compliant-ec2 as a tag value. As we defined in our tag policy, “non-compliant-ec2” isn’t compliant, so it should not allow the creation of an EC2 instance with this tag value.
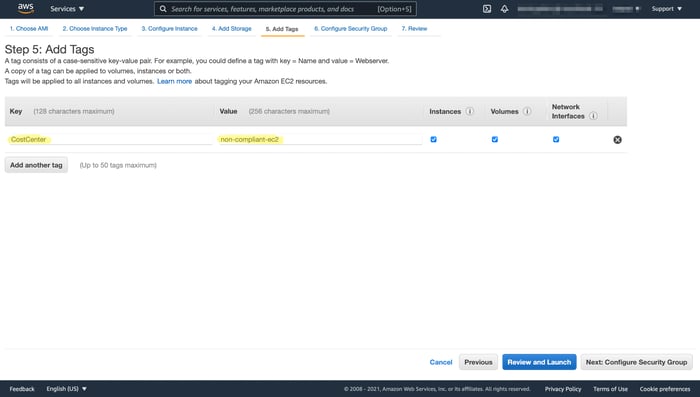 Example non-compliant tag value
Example non-compliant tag value
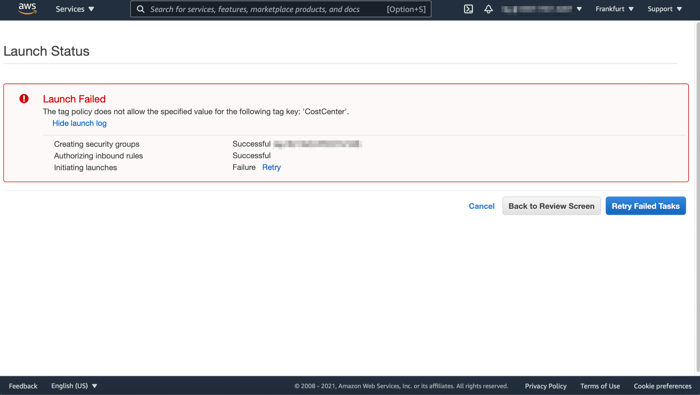
Creating an EC2 Instance with non-compliant tag key and value
It worked like a charm!
Now let’s try with a compliant tag value. As we defined in our tag policy, the tag value should be “bion-ec2-*” in this case, so let’s try it with the following tag value “bion-ec2-blog”.
Example compliant tag key and value
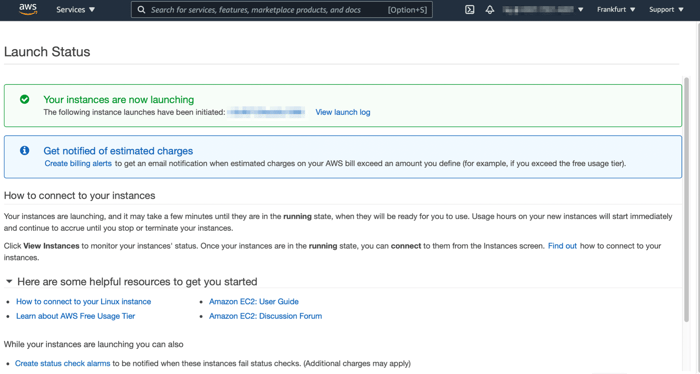
Creating an EC2 Instance with compliant tag key and value

We successfully enforced our tag policy, and now we have more control over our tagging strategy. I hope you found it helpful, and if you enjoyed reading it, please don’t forget to share.
In our second part of the blog post, we will do the same enforcement with Service Control Policies(SCPs) without the importance of tag values.
